Zero Trust Network Access (ZTNA) Solutions in Malaysia
SYSIT delivers enterprise-grade Zero Trust Network Access (ZTNA) solutions in Malaysia, enabling organisations to securely control access to applications and data based on identity, device posture, and context—without exposing internal networks or increasing ransomware risk.
Modern Access Security for Today’s Threat Landscape
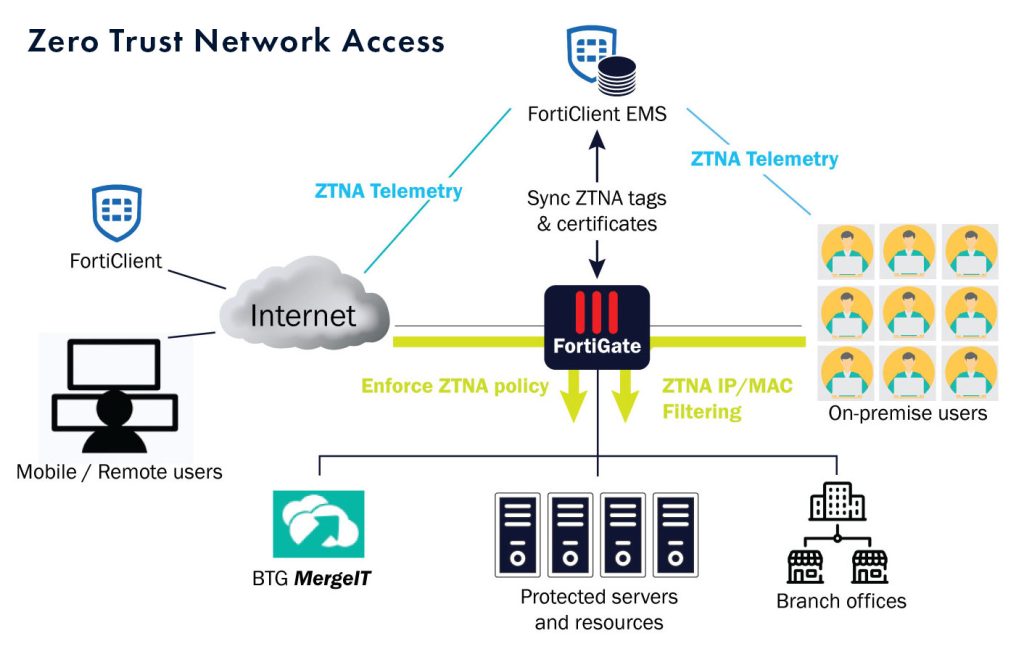
Why Traditional VPN Is No Longer Enough
Limitations of Traditional VPNs
Wide network access after login. Implicit trust once connected. Exposure of internal network resources. High ransomware and lateral movement risk. Limited visibility into application-level access
How ZTNA Improves Access Security
Application-level access only. Continuous identity and posture verification. No internal network exposure. Strong containment of compromised credentials. Audit-ready access visibility
SYSIT Zero Trust Network Access Capabilities
Identity-Based Access Control
Device Posture & Endpoint Validation
Application-Level Access Control
Cloud & On-Prem Application Protection
Micro-Segmentation & Lateral Movement Prevention
Visibility, Logging & Compliance
How SYSIT Delivers Zero Trust Network Access
Assess
Design
Implement
Optimise
Adopt Zero Trust Access with SYSIT
Ready to move beyond traditional VPN security? Contact SYSIT today to implement a Zero Trust Network Access (ZTNA) solution in Malaysia that protects your applications, users, and data—without sacrificing usability.

